Penetration tests – simulate the actions of a cybercriminal trying to gain access or take control over IT systems/ information from any place in the world. The aim of the tests is to check the resistance of mobile applications against security breaches and cyberattacks by conducting comprehensive tests compliant with: OWASP Mobile TOP 10 / OWASP MASVS/ OWASP Mobile Security Testing Guide. The tests are performed by experienced, professional security engineers, who hold numerous certificates, such as CEH, OSCE, OSCP, OSWE, OSEE, CISSP, CISA. Risks of security breaches resulting from identified vulnerabilities are assessed according to the globally recognised CVSS standard. Test results serve as a point of reference for managing risks and security incidents at the organisation. We have conducted such tests for banks, brokerages, leasing companies, energy providers, telecommunications service providers, producers, e-commerce businesses and others. More information can be found at http://optimapartners.pl/pl/projekty/projekty.
Benefits:
- Increasing the level of security of data processed in IT systems.
- Minimising the risk of security breaches and successful cyberattacks.
- Detecting current vulnerabilities, loopholes, errors in software and systems before they are detected by cybercriminals.
- Practical, implementable and cost-efficient recommendations (quick wins).
- Compliance with international norms and standards (ISO 27001, OWASP, OSSTMM, PCI DSS).
- Avoiding financial losses, reputational damage and legal consequences.
Types of tests:
- Black – box (no information about tested systems),
- Grey – box (partial information about tested IT systems),
- White – box (source code audits),
Approach
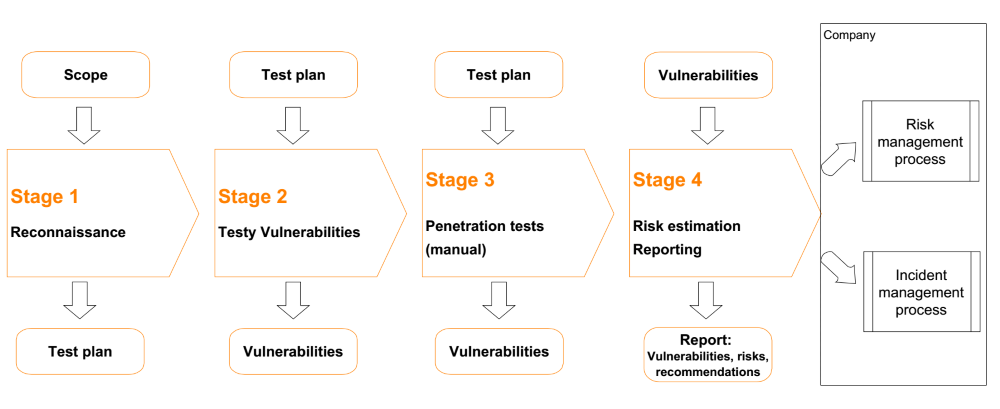
Automatic vs manual tests
Our methodology mainly focus on manual tests, which provide best quality. Around 70-90% of time is dedicated to manual tests performed by experienced security engineers. Even though automatic tests are very efficient, they generate a lot of false positives and do not guarantee detection of important vulnerabilities.
Tools
We use tried and tested tools for our tests, including commercial tools and ones designed by our security engineers. Our tools are designed and developed with specific systems and threats in mind to ensure their maximum efficiency during tests.
Reports
The results of our work are described in detail in a report, which usually consists of the following sections:
- Summary
- Detailed results, including:
- Aim
- Scope
- Approach, methods and tools
- Identified vulnerabilities
- Vulnerability detection method
- Evidence of vulnerabilities
- Security breach risk acc. to CVSS
- Recommendations
Test results are presented in detail and discussed during meetings with the client.
Recommendation deployment
In addition, we offer support with implementation of our recommendations, access to our security engineers and databases of information about vulnerabilities and ways of eliminating them.
