The aim of the analysis is to determine the perpetrators and/or consequences and scope of a breach by analysing traces of the breach, collecting evidence and implementing mechanisms minimising the risk of future breaches. The analysis is performed by experienced, professional security engineers, who hold numerous certificates, such as CHFI, CEH, CPTE, OSCP, OSCE, and who have experience in the scope of system security, system administration and software development. Risks of security breaches resulting from identified vulnerabilities are assessed according to the globally recognised CVSS standard. We have conducted such analyses for banks, brokerages, leasing companies, energy providers, telecommunications service providers, producers, e-commerce businesses and others. More information can be found at http://optimapartners.pl/pl/projekty/projekty.
Benefits:
- Increasing the level of security of data processed in IT systems.
- Minimising the risk of security breaches and successful cyberattacks.
- Detecting current vulnerabilities, loopholes, errors in software and systems before they are detected by cybercriminals.
- Practical, implementable and cost-efficient recommendations (quick wins).
- Compliance with international norms and standards (ISO 27001, OWASP, OSSTMM, PCI DSS).
- Avoiding financial losses, reputational damage and legal consequences.
Approach
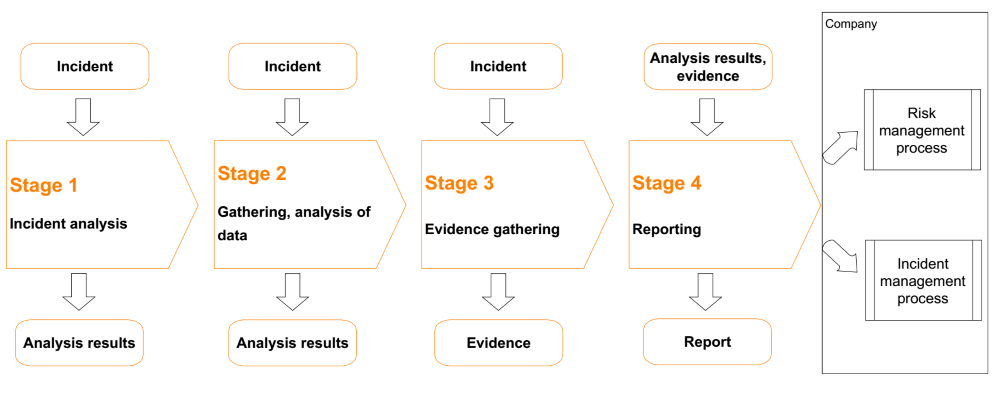
Tools
To perform the analysis, we use tried and tested tools, both commercially available tools and ones designed by our security engineers. Our tools are designed and developed with specific systems and tasks in mind to ensure their maximum efficiency.
Reports
The results of our work are described in detail in a report, which usually consists of the following sections:
- Summary
- Detailed results, including:
- Scope
- Results of breach traces analysis
- Collected evidence
- Recommendations
Test results are presented in detail and discussed during meetings with the client.
Recommendation deployment
In addition, we offer support with deploying our recommendations, access to our security engineers and information databases.
